Examples of reflected XSS signatures.

By A Mystery Man Writer
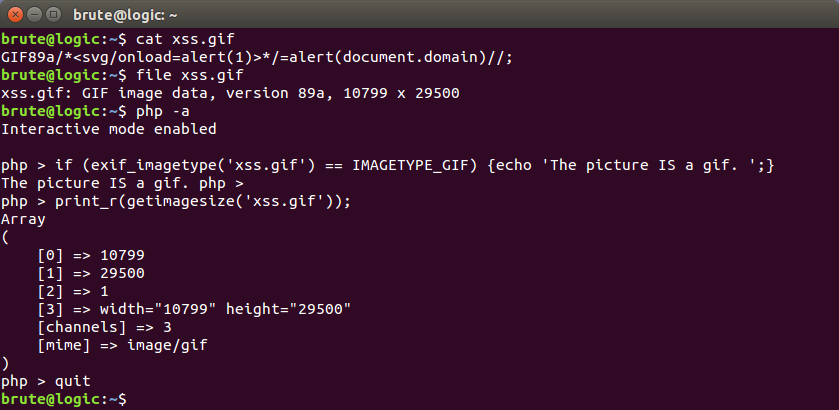
File Upload XSS - Brute XSS

A pseudo-code of the training dataset preparation. Fig. 5. The

PDF) Request and Response Analysis Framework for Mitigating Clickjacking Attacks

Available bandwidth estimates for different client buffer size and

Available bandwidth estimates for different client buffer size and

Let's Talk About Reflected Cross-site Scripting, by Fahri Shihab
JCP, Free Full-Text

Hossain SHAHRIAR, Associate Professor of Information Technology, PhD, Kennesaw State University, Georgia, KSU, Department of Information Technology
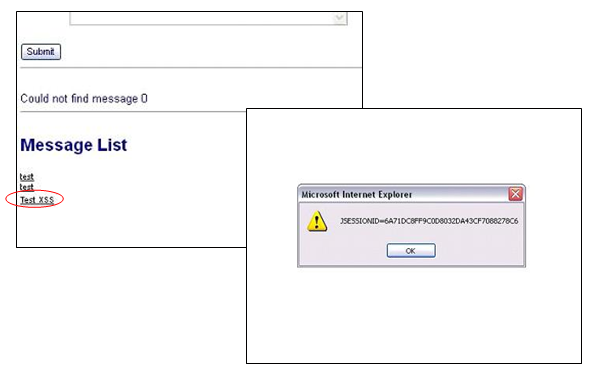
Common Web Application Vulnerabilities - Cross-Site Scripting

Amount of bytes transmitted in DNSKEY responses from TLDs, with and
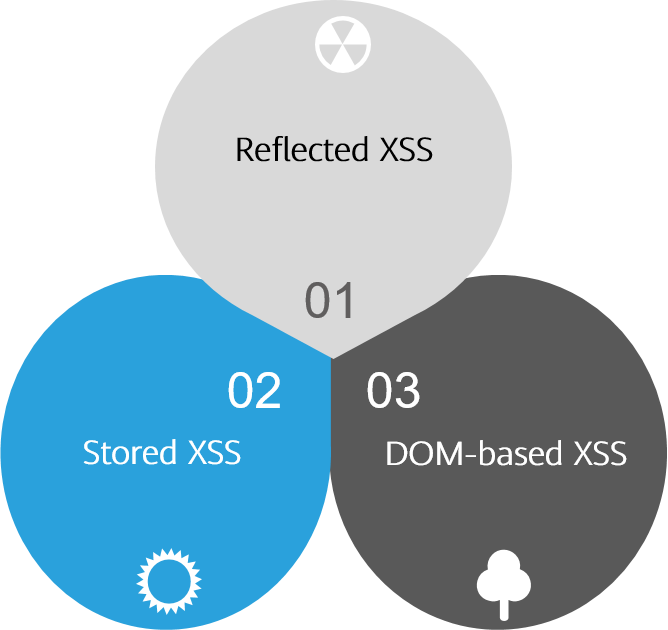
What Is an XSS Attack? How Do I Prevent XSS Attacks? - Huawei
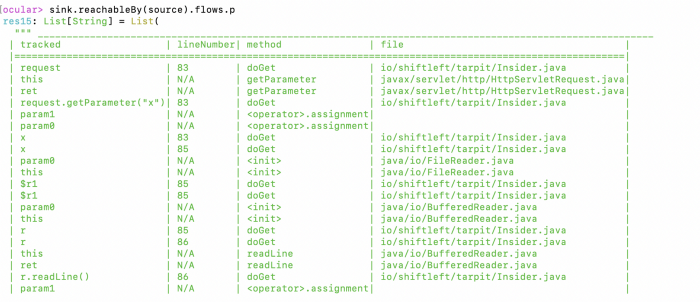
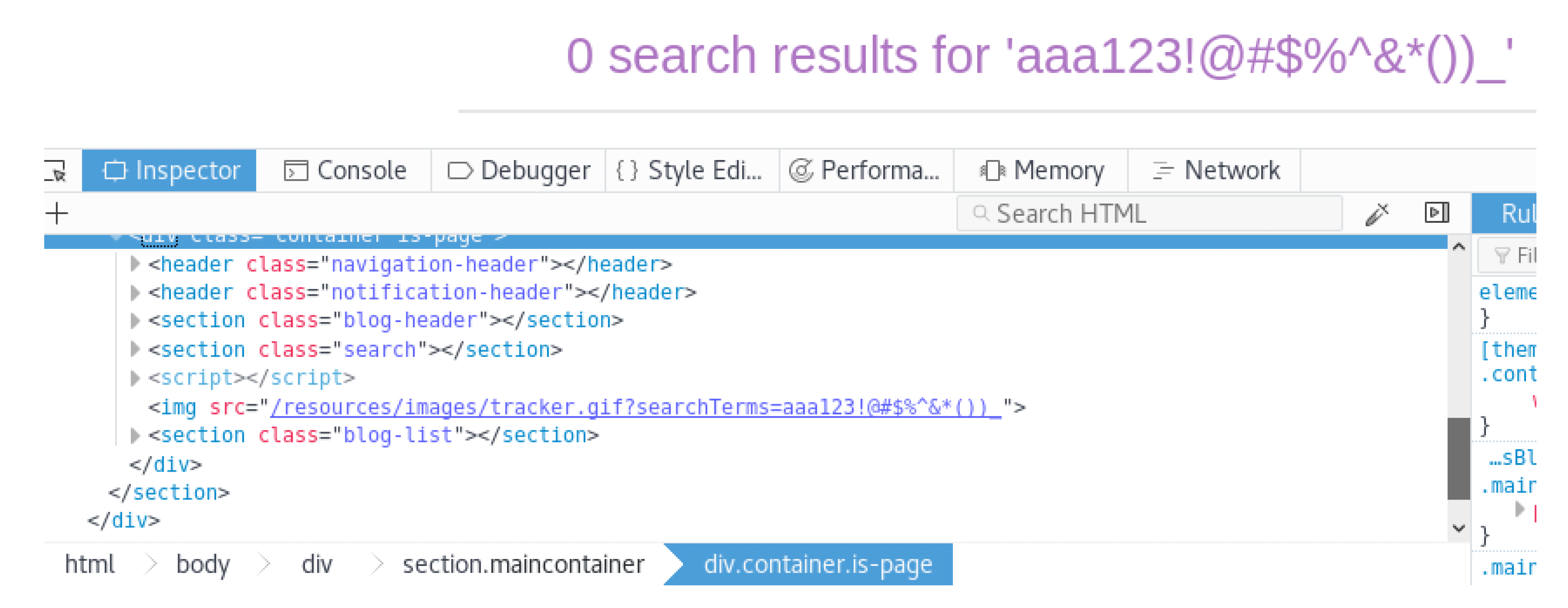
Discover Reflected XSS Candidates in Source Code with
- Purple Brand Hoodie 601 in Gray for Men

- Holabird Sports Reviews Read Customer Service Reviews of www. holabirdsports.com
- New Orleans Style Cafe Au Lait Recipe - Southern.

- Buy MODERN Little Girls Underwear Toddler Panties Cotton Boyshort Soft Boy Pants Kids Boxer Briefs kids underwear girls 6-Pack, Hello, 12-13 Years at

- Lace-Trim Microfiber Full-Cut Brief by Comfort Choice®